The benefits of using VPN gateways for remote access
What is a VPN gateway?
The VPN Gateway is a control point for data entrance to the network. When data introduce itself, VPN gateways decide whether to allow them or not. VPN gateway can take different forms such as a server, firewall, or router. Usually, VPN gateways come up as a router.
It connects devices, networks, and remote sites in a virtual VPN infrastructure. The main purpose is to secure devices, networks, and sites.
VPN gateway connects devices, networks, and sites in a virtual environment. It also creates communication between them. VPN gateway converts data, information, or other messages that are sent from one point to another. Essentially, it converts protocols and formats to advance secure communication and data transmission between the points.
A Virtual Private Network (VPN) is a security tool that creates a virtual tunnel and encrypts the incoming or outgoing data in networks.
By encrypting data, VPNs provide secure data transmission between the sources and the end-point. It secures the data path. A VPN gateway transfers this encrypted data to several locations such as cloud environments, private networks, and branch office data resources. A single VPN gateway can connect several devices, networks, and even different VPNs to each other.
You can learn more about VPN gateways and obtain further technical information by expanding your research. In this article, we will give brief and general information about VPN gateways.
Benefits of VPN gateways for remote access
● Enhanced Security
Enhancing security for remote access requires different tools and techniques. First of all, you need to understand how crucial remote access security is. The number of companies adopting remote or hybrid work models has been increasing today. It is natural that remote work requires remote access to company resources. There are several ways for the remote workforce to connect to company headquarter and obtain necessary information or data.
On the other hand, branch offices also connect HQ office resources remotely to operate their daily activities. All this remote access creates a security gap. First of all, remote access brings cloud environments into business life. Although keeping data, applications, and networks in the cloud is practical, it makes the company more prone to cyber-attacks.
It is more likely for cloud environments to fall victim to cyber-attacks and data breaches. This fact compels companies to look for advanced and new security solutions. They no longer rely on legacy security tools mostly based on hardware. Conventional safety tools may be adequate for the on-premises workforce, however, they can not fulfill the remote access security requirements of the companies.

Furthermore, data security is more vital in remote access. Millions of data have been transmitted over the Internet. Remote employees share vulnerable data, confidential information, and other delicate messages with each other every day. They also access vulnerable data resources of the company without any limitation.
However, data is the prior target for many cybercriminals because it is valuable in the dark web. Criminals can sell valuable data at high prices. On the other hand, data breaches can cause companies to lose their reputation and financial corruption.
The VPN gateway in remote work
The VPN gateways, by connecting on-premises devices and virtual networks through the Internet enhance security. The Internet is full of dangers and risks in terms of data breaches and cyber-attacks.
Defending company networks, data resources, and applications against Internet threats is vital for corporations. As the VPN gateway controls data entrance, malicious and prohibited data can not enter the internal network.
Network access control
Network access control is the core of any security implementation. If you monitor, observe, and control access requests and allowances, you can enhance your network security. It is about authorized access.
Only authorized and authenticated users should have access to the company resources. Unidentified or suspicious access requests must be denied to safeguard the vulnerable assets of your business.
● Improved productivity
Remote employees should have a reliable, safe, and scalable work environment. As a business owner, you must cut off their concerns about network and data security. First of all, companies should train their employees on data security, breach risks, and other crucial information. Without creating awareness, you can not expect them to comply with security policies.
When the remote workforce behaves according to the fundamentals, breach risk diminishes considerably. They do not lose time by using data breach cases or other related shortcomings. They can focus on only their missions in the company and increase their productivity. It is a fact that the clear mind of an employee creates better jobs.
Data breaches decrease and companies do not lose money on penalties or clients. They can create a respected market profile and increase their profits. Furthermore, they can invest to develop their business. The time and money that they save from data breaches can be converted into investments. In a long term, increasing productivity results in business growth.
● Cost savings
The VPN gateway saves companies from spending money on IT specialists, and several security tools. On the other hand, companies can save due to the VPN gateway avoid data breaches, and avoid companies to subject to penalties.
Also read : VPN and split tunneling: Power up your performance and security
VPN protocols for the VPN gateway
There are several VPN protocols that create standards for data transmission. According to the protocol type, data send and received at a different level of security and at different velocities. Protocols also matter in VPN gateways. Here we will discuss some protocols and whether they fit VPN gateways or not.
Internet Protocol Security (IPSec)
IPSec uses authentication and data encryption to provide security. Since authentication and data packet confidentiality is crucial in VPN gateways, IPsec can be considered in VPN gateways. In addition, IPsec makes use of site-to-site VPN to increase its functionality and compatibility.
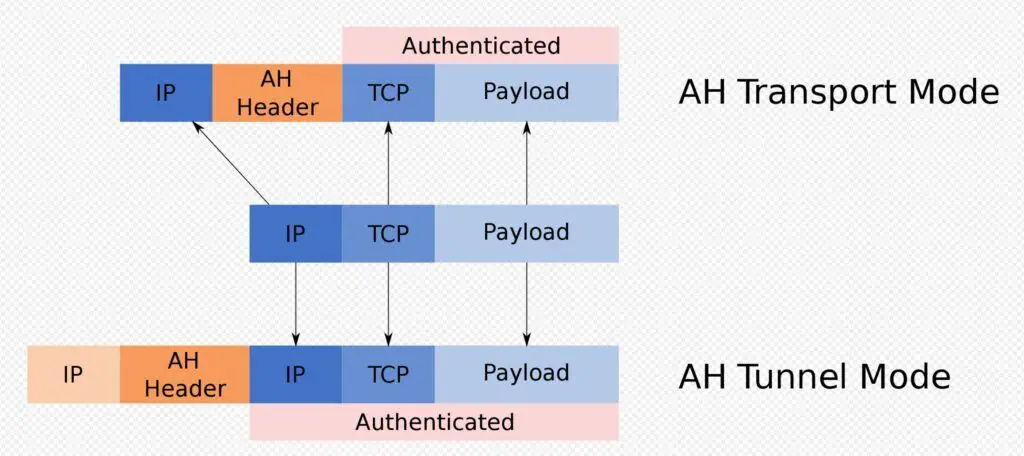
Point-to-point tunneling protocol (PPTP)
Point-to-point tunneling protocol is considered obsolete and not preferred in today’s VPN technology. This is because it has some security gaps and VPNs can not function well by adopting PPTP. So, PPTP is not suitable for the VPN gateway.
Layer 2 tunneling protocol (L2TP)
L2TP offers high security and is a good choice for VPN gateways. L2TP creates another virtual tunnel to provide encryption between two Layer 2 tunneling protocol tunnels. They do not encrypt data itself, they send it through another tunnel to encrypt and make it secure. Technically, it has a complex structure. However, this structure provides robust security for VPNs.
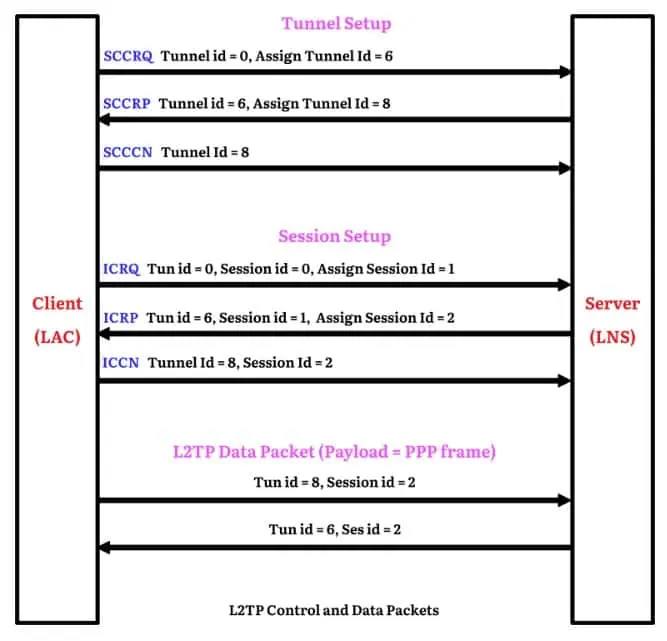
VPN protocols become important after you decide on the VPN type. Site-to-site VPN and remote access VPN require different protocols. So, before deciding on the type of protocol you must evaluate your business needs, weak points, security gaps, and other needs.
Last Words
Remote access is a quite new and developing area. This type of access requires further and advanced protection. VPNs are the most popular security tools for a long time. Here, VPN gateways have an important role to provide network and data security. The VPN gateways offer data safety, enhanced security, cost saving, and increased productivity.
As a business owner, you can decide on a VPN type by taking your business needs into account. Then you can choose the VPN protocol that fits best to your VPN technology. Relying on a VPN gateway can increase your business quality and makes you more compatible with security rules.