Tpm 2.0 & Windows 11: Why is it necessary? How to activate it?
Maximizing Security on Windows 11: The Importance of Activating TPM 2.0
TPM is a technology that provides hardware-based security features. It is used in computers and mobile devices to protect data stored on the device by encrypting it, making it difficult for attackers to access or modify the data.
Microsoft Windows 11 includes support for TPM 2.0, which provides additional security features beyond what was available in previous versions of Windows.
In this article, we will discuss why TPM 2.0 is necessary on Windows 11, how to activate it, and the benefits of using it.
- TPM 2.0 is designed to provide a secure boot environment and enhanced encryption capabilities for data stored on a device
- It stores cryptographic keys used for user authentication and data encryption, and supports biometric authentication methods and two-factor authentication
- The TPM 2.0 technology also supports virtualization, allowing multiple operating systems to run securely on a single computer.
- This version of TPM enhances security for both individual users and enterprise organizations by providing strong encryption, biometric authentication, and secure boot capabilities.
What is TPM 2.0 and what is it used for?
TPM 2.0 is an evolution of the Trusted Platform Module (TPM) 1.2 specification, released in 2006 by the Trusted Computing Group (TCG).
It is a hardware-based security chip that provides:
- a secure boot environment for your computer,
- as well as enhanced encryption capabilities for data stored on the device.
The hardware chip also stores cryptographic keys which are used to authenticate users and encrypt data stored in the system memory or hard drive.
TPM 2.0 allows improved authentication by using biometric information such as:
- fingerprints,
- facial scans,
- as well as two-factor authentication using passwords, smart cards, and other forms of verification.
In addition, TPM 2.0 adds support for virtualization, allowing multiple operating systems to run simultaneously on a single computer while keeping each one separate and secure from the others.
Why is TPM 2.0 necessary on Windows 11?
TPM 2.0 is necessary because it adds an additional layer of security beyond what was available with previous versions of Windows 10 or earlier versions of TPM 1.2 chipsets found in some machines manufactured before the 2019-2020 timeframe.
The added protection comes in several forms including:
- Secure Boot: With this feature enabled via TPM 2.0, each time you boot up, Windows will check whether all components are properly signed by Microsoft before loading them into memory for execution;
this makes sure no malicious code can get past this initial verification process which could potentially cause harm to your computer’s operating system or steal sensitive information stored on the device.
- Data Encryption: With TPM 2.0 chipsets activated via TPM 2.0 firmware update you can use BitLocker Drive Encryption technology which provides advanced AES 256-bit encryption capabilities for protecting data stored both online and offline.
- Authenticate Users: Thanks to two factor authentication enabled via TPM2.0 chipsets you can use biometric information such as fingerprints or facial scans in order to securely log into systems without having passwords compromised.
This ensures only authorized users can gain access while still providing convenience through biometric authentication methods
How does TPM 2.0 enhance the security of the system and data?
With new features added with every version release of Microsoft Windows 11, its security capabilities continue to increase with each iteration.
By enabling support for virtualization technologies like Hyper-V, along with leveraging industry standard protocols, organizations can now provide increased levels of security for their valuable assets.
Additionally, through built-in support for two factor authentication methods like biometrics, these organizations can ensure that only authorized personnel have access while also providing an added layer of convenience.
Furthermore, utilizing secure boot through TPM2.0 chipsets ensures that only secured programs are allowed execution following an initial verification process which helps prevent malicious actors from gaining unauthorized access.
Finally, by enabling these various features, organizations are able maximize their security posture while also increasing their operational efficiency.
What are the benefits of TPM2.0 for the user and enterprise?
- For individual users, leveraging the enhanced security features provided by TPM2.0 helps provide confidence that their personal data remain secure even if their device were stolen.
By utilizing strong encryption protocols like AES256 – bit combined with technologies like BitLocker Drive Encryption paired with biometric authentication methods, users can rest easy knowing that their information remains private from prying eyes.
- For enterprise organizations, leveraging TPM2.0 helps build trust between themselves and their customers / clients through increased levels of assurance surrounding their products / services offered .
This trust translates into tangible business value since customers want assurance that their privacy remains intact when working with these organizations.
Additionally , when utilizing TPM2.0 along with virtualization solutions like Hyper – V companies are able to improve upon existing operational efficiencies while also reducing costs associated with server infrastructure maintenance down long term.
How can you check that TPM is activated ?
To check if TPM is activated you have to:
- Press the Windows key + R to open the “Run” dialog box.
- Type “tpm.msc” and click “OK” to open the “TPM Management” console.
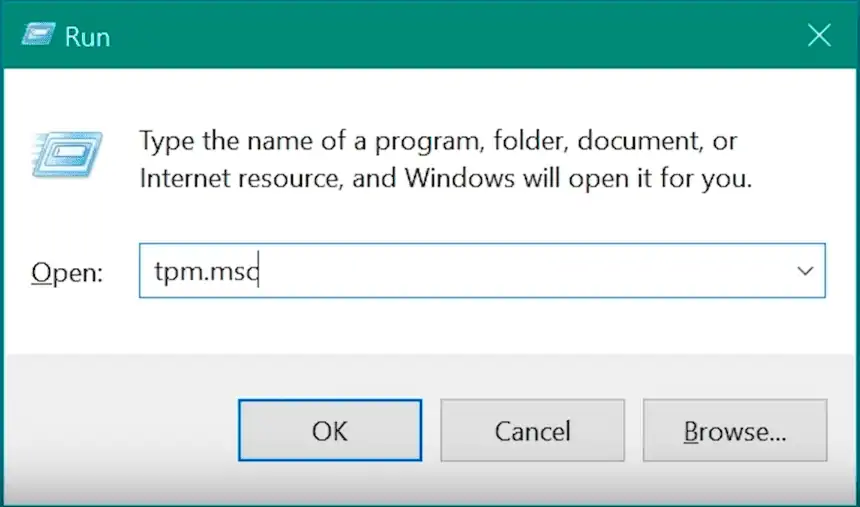
Once in the TPM management console you will see this window if TPM is not enabled or not available on your motherboard.
If it’s activated, then, this window will appear:
TPM 2.0 is not activated? Don’t panic, we will show you how to activate it.
How To Activate TPM2.0 On Windows 11?
Before activating TPM2.0 there are some prerequisites that must be met first:
- firstly ensure that TPM1.2 chipset has been replaced with TPM2.0 chipset if applicable;
- secondly verify that UEFI Firmware Settings have been updated accordingly;
- finally ensure proper installation / configuration has taken place before attempting the activation process itself.
After all requirements have been met then follow below steps to activate TPM2.0 in BIOS:
Step 1: Restart your computer and press the appropriate key to enter the BIOS setup. The key to enter the BIOS is usually displayed on the screen during the boot process and is specific to your computer’s manufacturer.
Step 2: Navigate to the “Security” or “Advanced” tab in the BIOS setup.
Step 3: Find the option to enable TPM 2.0 and set it to “Enabled”. The exact location of this option may vary depending on your BIOS version and manufacturer.

Step 4: Save your changes and exit the BIOS setup.
Note: If you are unable to initialize the TPM, you may need to clear the TPM first. To do this, follow the instructions provided by your computer’s manufacturer. You may also need to enable the TPM in the BIOS setup on your computer.
Conclusion : Why Is It Important To Activate TPM2.0 On Windows 11?
By leveraging the enhanced security protocols provided by the recent release of Microsoft Windows 11, you can now enjoy increased level protection across all platforms due to careful implementation of TPM 2.0.
- By activating TPM 2.0 on your Windows 11 system, you can ensure that your data and system are protected against security threats.
- This is especially important for businesses, which can be exposed to significant risks in the event of a data security breach.
- When TPM 2.0 is activated on their Windows 11 systems, users and businesses can enjoy increased security without having to worry about protecting their data.